 Every day, we use the internet to find information, make purchases, socialize and learn. However, for most people, much of the internet remains hidden from everyday view. This hidden layer is the dark web — and it presents a significant threat to public safety agencies.
Every day, we use the internet to find information, make purchases, socialize and learn. However, for most people, much of the internet remains hidden from everyday view. This hidden layer is the dark web — and it presents a significant threat to public safety agencies.
To help agencies combat this threat, the Public Safety Threat Alliance (PSTA) established a no-cost dark web monitoring service in 2024 that alerts members if any compromised credentials associated with them are found.
In this blog, we’ll take a deeper look at the dark web. We’ll discuss why it poses a risk to public safety agencies as well as what actions you can take now to reduce that risk.
The three layers of the web
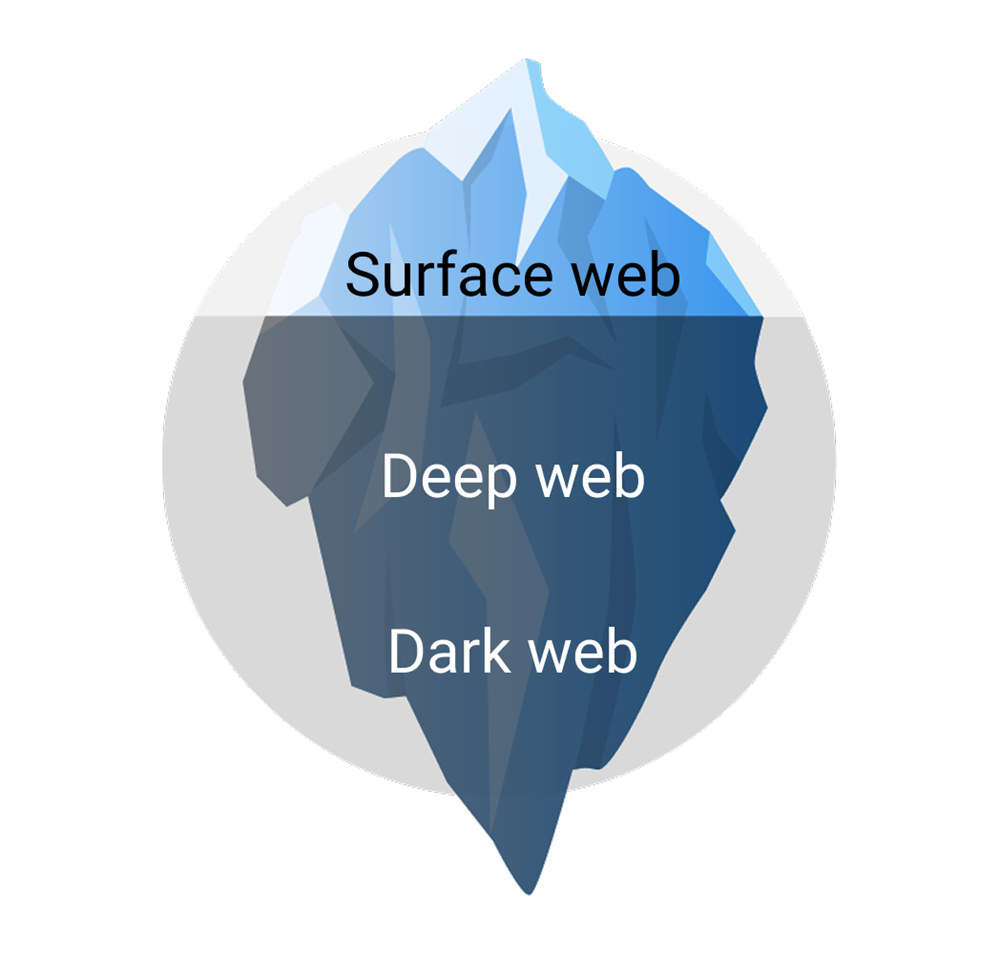
The internet can be likened to an iceberg, with three distinct layers: the surface web, the deep web and the dark web.
- Surface web: This is the internet we use daily, including search engines, research sites such as Wikipedia and news outlets.
- Deep web: These pages are hidden from standard viewing but aren’t necessarily malicious. Examples include medical records, legal documents, scientific reports and password-protected subscription services such as Netflix.
- Dark web: Lying within the depths of the deep web, the dark web is a hazardous area of the internet accessible only through specialized software, such as The Onion Router (Tor). This hidden layer is estimated to be approximately 5,000 times larger than the surface web, with a staggering 60 percent of its content dedicated to illicit activities.
The dark web operates as an anonymous marketplace, fueling a global cybercrime economy estimated to be worth $1.5 trillion annually. Criminals trade stolen data, illegal and black market drugs, sophisticated malware and illicit services with ease.
A shadow over public safety
For public safety agencies, the dark web isn’t just a hypothetical cyber threat. It’s often the source of attacks that jeopardize mission-critical systems and the communities they serve.
The consequences of stolen data being traded on the dark web can be severe. This stolen information can be used for targeted social engineering attacks, allowing adversaries to impersonate officials, manipulate personnel or gain further unauthorized access to systems.
If the personal details of law enforcement officers are exposed, it puts them and their families at risk of harassment, doxxing, or even physical harm. Such breaches erode public trust in an agency’s ability to protect sensitive information, hindering community cooperation and engagement. Ultimately, these incidents can divert valuable resources towards incident response and recovery, rather than proactive public safety initiatives.
Cybercriminals use the dark web to:
- Trade stolen credentials, distribute malware and exploit kits: The low cost of stolen credentials and readily available Malware-as-a-Service (MaaS) tools on the dark web has democratized cybercrime, significantly increasing the risk of devastating attacks on vital public safety and emergency networks. These cheap yet potent resources empower even unsophisticated actors to compromise critical systems, posing a severe threat to public welfare.
- Share vulnerabilities: Discussions and sales of zero-day exploits or vulnerabilities in standard software allow attackers to target systems before patches are available.
- Plan and coordinate attacks: Although sensitive communications often occur on encrypted chat channels, the dark web remains a platform for threat groups to publicize victims and coordinate broader campaigns.
The problem: valid credentials as a primary access vector
The PSTA consistently identifies credential abuse, including the use of compromised valid usernames and passwords to access accounts and escalate privileges, as the primary initial access technique for cyber threat actors targeting U.S. public safety mission-critical systems.
Threat actors frequently obtain these compromised credentials by purchasing them from dark web marketplaces and criminal forums. This strategy is highly effective as it allows adversaries to appear as legitimate users, bypassing security measures and leveraging other operational vulnerabilities, including shared accounts and a lack of multi-factor authentication (MFA).
The PSTA’s dark web monitoring service
Cyberattacks pose a critical and evolving threat to public safety agencies. When threat actors gain an initial foothold, they can access and download sensitive data and even move laterally into sensitive public safety networks. This can severely disrupt critical operations like computer-aided dispatch (CAD), public safety radio and 9-1-1 emergency call handling.
To help combat the threat of compromised credentials, the PSTA established its no-cost dark web monitoring service in 2024. PSTA members are eligible to add their organization’s domains and agency names into the PSTA’s own intelligence collection plan, which scours criminal marketplaces, encrypted criminal messaging channels and top malware operations.
This service allows members to be immediately alerted if any agency employee has their credentials compromised or stolen, so IT defenders can rapidly change them to help prevent a breach. To date, the PSTA dark web monitoring service has alerted its members to 1,770 validated stolen credentials since its inception in early 2024.
About the PSTA
The PSTA, established by Motorola Solutions in 2022 and recognized by CISA, is a collaborative organization that empowers agencies and members to share vital cybersecurity threat information, boosting collective awareness and readiness. Through shared threat insights, we can collectively fortify defenses against these constantly evolving cyber threats. Join the PSTA today to contribute to a safer, more secure public safety community and get access to no-cost threat intelligence products and services, including dark web monitoring.




