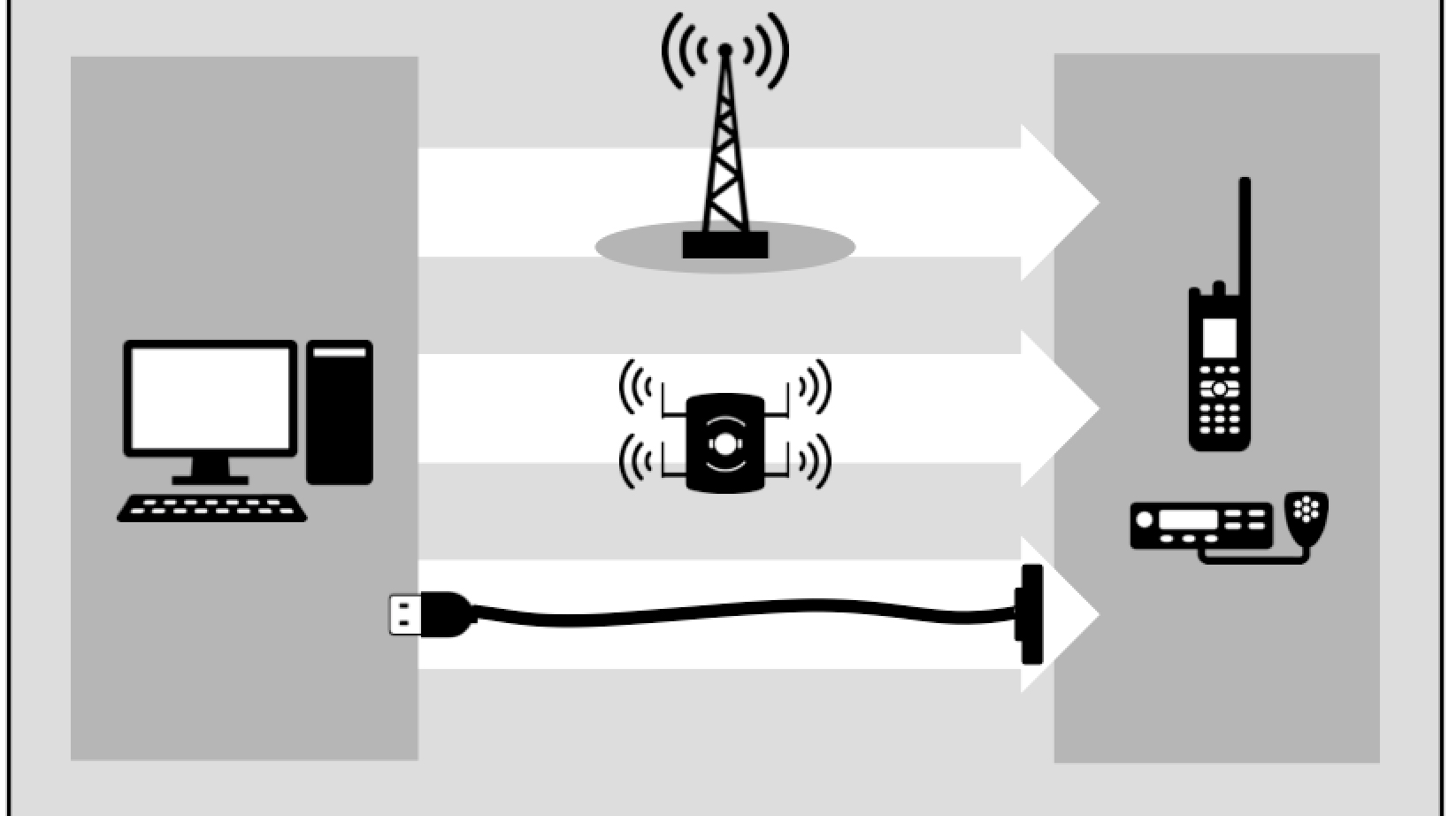
The Industrial Internet of Things (IIoT) is the environment where smart sensors connected to objects give those objects a ‘digital voice’. It’s a voice that allows them to autonomously connect and share data with one another – and the back office – over an IP connection. With the increased adoption of IIoT, the world is becoming more connected, presenting great benefits for communication efficiency, but also posing significant risks when bridging technologies that were not initially designed for such connectivity.
Every company is susceptible to cyber attacks. There are various motives for and mediums through which people can wrongfully access a network. When this is applied to industries that rely on SCADA or machine-to-machine (M2M) communications–like oil and gas, utilities, water/wastewater and mining–the risk is amplified, as those operations were not initially built for this new highly connected world. While this danger is real, so are the solutions to keep an agency protected. Take the following scenarios for example:

Cause: A disgruntled insider with a malicious motive to hurt the organization, or an unknowing team mate that accesses confidential information on an unsecure wifi hotspot brings malware into the network.
Effect: Control systems that were designed to be easily customizable, and many newer solutions which are standards-based and “off the shelf”, are vulnerable to malware attacks because they have multiple points of entry, or are built on open platforms that are more easily accessible in this IP environment. Production slows or comes to a halt, and results in an average cost of $213,542 per attack to a company.
Solution: Basic security measures, like firewalls, antivirus software, encryption, unused port deactivation, and secured programming can help keep authorized personnel in control and information secure.
Cause: Criminals, enemy states, or industry competitors looking for proprietary intelligence or financial information phish for information by using fake usernames, accounts, or requests for details under the illusion of being trustworthy.
Effect: A “not-so-closed” network, or a workforce uneducated on phishing risks share sensitive information, putting people and operations in danger, at an average cost of $45,959 per attack to a company.
Solution: Enabling access controls, which can be general, or role-based, identifying intrusions with man-in-the-middle protection and educating employees on the risks can protect information from seemingly “safe” impostors.
Cause: Bot-Networks run by lone programmers or the cyber underground use advanced persistent threats (APT) to coordinate attacks on a system for glory, financial gain, or simply to disrupt normal service.
Effect: With intrusions coming from multiple angles, systems built with a single security layer, or with lack of security within the system itself are easily exploited, and an entire operation can go down, or become controlled by outsiders.
Solution: Set firewalls, monitor activity, whitelist authorized applications, and regularly audit data for abnormalities. This keeps you aware of who is traversing your system, and when an intruder seeks unauthorized access.
Cause: For the thrill of disrupting others, as a part of a larger scale attack, or to just intentionally wreck havoc, terrorists can paralyze a network.
Effect: A denial of service attack can incapacitate a system by inundating it with useless traffic. It exploits weaknesses in the system to disrupt operations, at an average cost of $166,545 per attack to companies.
Solution: Attacks with pure mal-intent are often highly sophisticated, but application control software (whitelisting software) allowing only pre-identified programs to run and time-window command limits can block pernicious activity.
The Industrial Internet of Things (IOT) has the potential to revolutionize operations by automating complex processes, communicating data to teams in the field or back office, alerting of potential issues before they come to fruition and enabling organizations to take greater control to work smarter. However, if a system is not prepared for increased connectivity, the results can be disastrous.
Fortunately, as connectivity has improved, so have the ways to keep information and operations secure. Motorola’s ACE3600 aims to make automation and monitoring of your complex processes seamless and secure with a variety of security features built in and certified both internationally and domestically. Furthermore, by running your SCADA or M2M data over an ASTRO 25 network you can take advantage of many of the same end-to-end security features applied to your voice communications.
Learn more about the ACE3600, our secure networks and Motorola’s entire IIoT portfolio by visiting www.motorolasolutions.com/industrialiot.