Cyber crime is on the rise. Recent reports highlight an increase in the number of U.S. data breaches by nearly 45 percent. As reports of cyber attacks continue to make headlines, organizations are increasingly looking at ways to protect themselves. The result is an increased investment in cybersecurity tools and programs. By the year 2021, it is estimated that global spending on cybersecurity products and services will reach a cumulative $1 trillion.
Despite these increased investments, security capabilities have been unable to deliver the desired efficiency and effectiveness. Currently, businesses are investing in a wide variety of cybersecurity tools, including advanced perimeter controls, encryption, automated policy management and threat intelligence systems.
However, spending on cyber tools alone does not ensure security. A truly effective cybersecurity program evaluates risk and then integrates the right technology with people and processes. Understanding your organizational risk is critical to making smart decisions regarding cybersecurity tools and technologies. The most important thing any decision maker does is determine how to allocate their resources towards the success of their organization’s mission. So, how do you know if you are doing that?
Currently, a study by the Ponemon Institute highlights a potential disconnect in organizational spend on cybersecurity technology with actual return on investment (ROI). Many organizations are investing heavily in a few targeted technologies – including compliance and automated policy management – overlooking the need for a more balanced portfolio of technologies.
While these technologies do play a critical role in cybersecurity, they should be augmented with security systems that include risk monitoring, patching and innovations like cyber analytics and machine learning. These technologies have shown a high return on investment with the breakthrough areas of cyber analytics, user behavior analytics, automation and machine learning ranking in the top four cost-saving security technologies. Organizations should also work to ensure they take full advantage of their solution capability – employing, maintaining and operating it properly to achieve success.
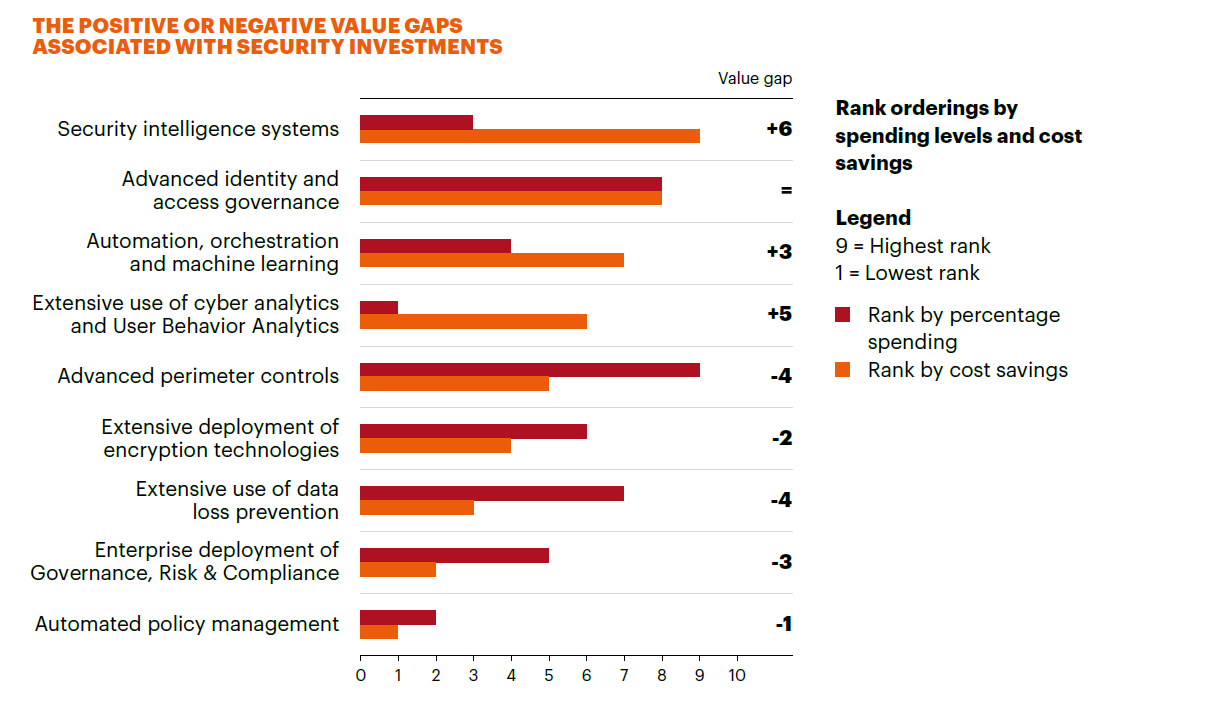
As the cyber threat landscape continues to evolve, investments in cybersecurity need to be closely monitored and adjusted to ensure organizational spend is being allocated appropriately. Organizations need to build an ecosystem that encompasses a diverse portfolio of cyber tools that can be integrated to work together. By balancing a strong foundation of “basics” – such as security intelligence, patching and advanced access management – with innovations like analytics and machine learning, organizations can improve the effectiveness of their security programs.
But technology alone doesn’t ensure security. Organizations need a culture of good security processes and a team of well-trained professionals to drive their cybersecurity efforts. A security team can help guide practices, prioritize activities, respond to threats and inspect potential risks. However, security must live throughout an organization – with processes that safeguard critical communications and proactively monitor for risk. This includes looking at existing vulnerabilities, fixing them, assessing risk and developing a response and recovery plan.
Cybersecurity doesn’t happen by chance. It requires a focus on implementing the right technologies, engaging with knowledgeable people and implementing effective processes. Read the full Motorola Solutions White Paper here for insights into how implementing a holistic, risk based approach can help your organization address the growing cybersecurity challenge.




