Thousands of articles, 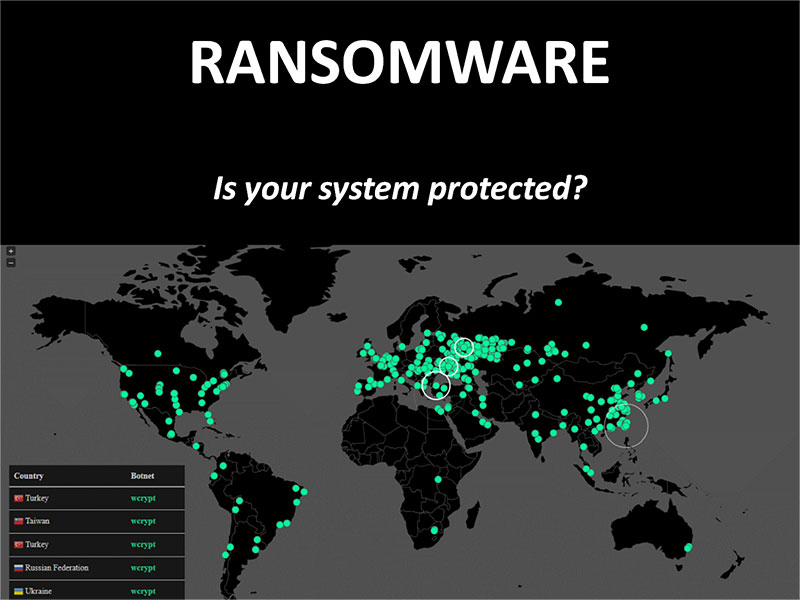 videos and blogs have been written about the importance of software security patching. The simple fact is that most cyber-attacks are based on known system and software vulnerabilities. Patching can correct these vulnerabilities and safeguard your network from intrusions, such as ransomware.
videos and blogs have been written about the importance of software security patching. The simple fact is that most cyber-attacks are based on known system and software vulnerabilities. Patching can correct these vulnerabilities and safeguard your network from intrusions, such as ransomware.
And yet around the world, many of us fail to make security patching a priority. This became eminently clear over the weekend in the largest cyber-attack ever. A ransomware known as “WannaCry” resulted in more than 45,000 attacks in at least 100 countries over a 48-hour window. Former Assistant Attorney General for National Security John Carlin stated, “The reason this is hitting so many computers at once is they [the hackers] discovered a vulnerability in the most popular operating system in the world…in Microsoft Windows.”
Companies that were up to date on their patching were not affected by the cyber attack that shocked not only private organizations such as telecom giant Spain’s Telefonica, but also government and public safety mission-critical entities such as hospitals and clinics across the United Kingdom and the Andhra Pradesh police in India.
“The fact that so many organizations were vulnerable to this was quite a surprise,” said cyber expert and CEO of Capital Alpha Security in the United Kingdom Matt Tait. “This patch came out three months ago.” Yes, Microsoft did announce a fix for the vulnerability, but not everyone acted or even took note when the announcement was made. Some were unaware. Others had budget or resource constraints or simply waited to address due to other priorities.
The main lesson from WannaCry outbreak? Don’t delay patching–ever. The political, public relationship and most important, civilian ramifications are enormous, especially for mission-critical organizations that depend on sophisticated IP-based communication networks. Our dedicated security experts help our customers mitigate cybersecurity threats with validated security patches through our Security Update Service (SUS). We analyzed, vetted and released the patch which addressed the WannaCry vulnerability to our customer base shortly after its initial release by Microsoft. We installed it and others for customers who opt for remote security patching and encourage those with our self-install patching option to do so immediately and reboot servers if you already haven’t.
The good news is that a security researcher inadvertently discovered a ‘kill switch’ which has halted the spread of the initial worm that took the world by surprise. In our modern world of cyber-threats, none of us can afford to be complacent any longer. Security patching is one of the core, fundamental steps needed to safeguard your system from cyber threats. For more information, visit our cybersecurity services page.