 If your organization has ever wondered whether it is making measurable progress in combating cyber crime, you’re not alone.
If your organization has ever wondered whether it is making measurable progress in combating cyber crime, you’re not alone.
The emergence of new technologies have lowered the bar for modern cybercriminals, expanding the cyber crime landscape beyond a limited group of skilled individuals. This widening pool of cybercriminals is creating new vulnerabilities and new threats on an almost daily basis. Amid this evolving reality, it can be difficult to keep up.
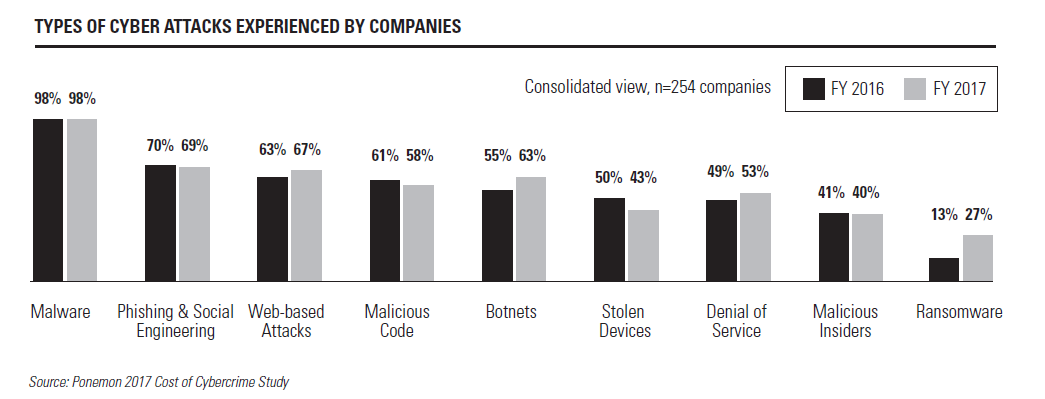
According to the seventh annual Allianz Risk Barometer Survey, cyber risk is now one of the top two global business risks. And there are a number of specific attack avenues organizations are increasingly concerned about:
- Malware: Fake download links and phony email attachments – we’ve all seen them. When successful, these malware attacks enable criminals to take control of your machine, monitor actions and keystrokes, and send confidential data from your computer and network. Despite our knowledge of these sorts of attacks, nearly 100 percent of companies report having experienced some form of Malware crime. A recent malware attack on Allentown, Pennsylvania struck the city’s most critical systems – including surveillance camera networks – costing nearly $1 million and forcing the shutdown of some public safety operations.
- Web-Based Attacks: Much like malware, the majority of organizations have experienced a web-based attack. Unfortunately, these types of crimes can cost companies 100 times more than malware annually. In fact, one recent event saw hackers steal 45 million records, costing the affected organization nearly $260 million.
- Botnets: Blending the words “robot” and “network,” botnets are a network of “bots” that criminals can remotely manage to deploy malware, initiate attacks on websites and steal personal information. These attacks can infect a multitude of devices – devastating an organization. In fact, the recent Mirai botnet saw the shut down of major areas of the internet, including Twitter, Netflix and CNN, as well as the entire country of Liberia.
- Lost and Stolen Devices: We do everything on our mobile devices and laptops – send emails and text messages, conduct banking, store personal and corporate information and more! With this wealth of information available, it’s no wonder that nearly 54 percent of the major data breaches tracked by federal regulators since 2009 have been the result of lost or stolen devices.
- Denial of Service (DoS): Have you ever tried to access a website and failed? Ever tried to reach a number and got a busy signal? The website or phone line may have been the victim of a DoS attack. These attacks overload an organization’s web or telephony service, flooding it with more traffic than it can withstand. As a result, visitors attempting to access the service are unable to view its content or make a call. That was the case with recent attacks on administrative public safety answering points (PSAP) and emergency communications centers. Perpetrators launched a high volume of calls against the target networks, tying up the service and preventing legitimate calls.
- Malicious Insiders: Taking a step beyond insider threats caused by employee negligence, malicious insiders include current or former employees, contractors or business associates looking to gain access to insider information on security practices, data and computer systems. These attacks are difficult to detect and remediation can be extremely costly – with fifty-three percent of companies estimating remediation costs of $100,000 or more and 12 percent estimating a cost of more than $1 million.
- Ransomware: Much like it’s name conveys, ransomware takes over a computer and denies access to data unless a ransom is paid. These attacks pose a serious organizational threat, with more than one-quarter of cyber insurance claims resulting from ransomware attacks. And no one is immune. In 2017, WannaCry ransomware hit a number of high-profile targets around the world – impacting more than 300,000 organizations worldwide, with victims receiving a note demanding a ransom of $300 in bitcoin. PSAPs are not immune. Baltimore’s 9-1-1 dispatch system recently experienced a ransomware attack, with hackers infiltrating a server that runs the city’s CAD system for 9-1-1 and 3-1-1 calls, causing the city to revert to manual dispatching for nearly 24 hours. This attack is just one of a recent slew of attacks targeting municipal systems across the country.
In the world of cybersecurity, things are changing at a rapid pace. And while organizations continue to acknowledge the importance of protecting their networks, keeping up with reality can be a challenge. That’s where cyber “resilience” comes in. Moving beyond individual cybersecurity efforts, resilience looks at security as an integral part of an organization’s core business – enabling them to better prepare, prevent, respond and recover from cyber breaches.
Read the full Motorola Solutions White Paper here to learn more about cyber resilience and how your organization can better protect against the growing cyber threat.
Attending APCO? Please join me during the Cybersecurity information track (August 6, 4:30 – 5:30 PM) when I will present “Welcome to the ‘No FUD’ Zone”. During my talk I will explore real events, real impacts and offer a view of the trends in public safety technology to combat cyber threats, as well as what Public Safety personnel can do to help manage the risk.



Richard Stewart
March 6, 2025
This great information and will be disseminated to our statewide stakeholders as we provide Incident Response and Cyber Threat Protection (SOC/SIEM) and related outreach here in Mississippi. Thank you for sharing!